New AitM Phishing and BEC Attacks Targeting Banking and Financial Services
Attention: Urgent Security Advisory
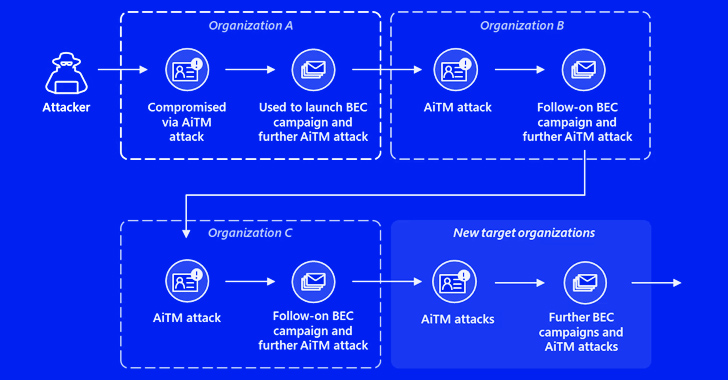
Microsoft has recently revealed a concerning trend in the cybersecurity landscape: a new multi-stage adversary-in-the-middle (AitM) phishing and business email compromise (BEC) attack targeting banking and financial services organizations.
This attack, tracked under the name Storm-1167, involves a compromised trusted vendor and sophisticated techniques such as indirect proxy usage. By leveraging an indirect proxy, the attackers were able to create tailor-made phishing pages and carry out session cookie theft, demonstrating the advanced nature of AitM attacks.
In this attack, the perpetrators utilized a website that mimicked the sign-in page of the targeted application, hosted on a cloud service. This fraudulent sign-in page loaded resources from an attacker-controlled server and initiated an authentication session with the victim's credentials on the authentication provider of the target application.
The attack chain begins with a phishing email that redirects victims to a spoofed Microsoft sign-in page, where they unwittingly enter their credentials and time-based one-time passwords (TOTPs). The harvested information is then used to impersonate the user and gain unauthorized access to their email inbox through a replay attack. Once inside, the attackers exploit the compromised account to access sensitive emails and orchestrate a BEC attack.
In addition, the attackers add a new SMS-based two-factor authentication method to the target account, enabling them to sign in using the stolen credentials without raising suspicion.
In a case analyzed by Microsoft, the attacker launched a mass spam campaign, sending over 16,000 emails to the compromised user's contacts, both within and outside the organization. The adversary also took steps to minimize detection and establish persistence by responding to incoming emails and subsequently deleting them from the compromised mailbox.
The complexity of AitM and BEC threats is highlighted in this attack, which exploits trusted relationships between vendors, suppliers, and partner organizations for financial fraud purposes.
Less than a month ago, Microsoft warned about the increasing prevalence of BEC attacks and the evolving tactics employed by cybercriminals. These include the use of platforms like BulletProftLink for large-scale malicious mail campaigns and the use of residential IP addresses to make attacks appear locally generated.
It is crucial for banking and financial services organizations to remain vigilant, implement robust security measures, and educate employees about the risks associated with phishing and BEC attacks.
Comments
Post a Comment