In recent years, secure boot technology has become increasingly important for protecting computer systems against malicious attacks. Secure boot is a feature in the Unified Extensible Firmware Interface (UEFI) that ensures that only trusted software is loaded during the boot process. Secure boot has been included in Windows operating systems since Windows 8 and has been a key component of Microsoft's defense-in-depth security strategy.
However, researchers have recently discovered a new UEFI bootkit malware called BlackLotus that is capable of bypassing secure boot on Windows 11. This marks the first time that a UEFI bootkit has successfully bypassed secure boot on the latest version of Windows.
What is a UEFI Bootkit?
A UEFI bootkit is a type of malware that infects a computer's UEFI firmware, which is responsible for initializing hardware components and starting the boot process. Once a UEFI bootkit has infected a computer, it can load malicious code during the boot process before the operating system even starts.
UEFI bootkits are considered some of the most dangerous types of malware because they are difficult to detect and remove. Because they operate at such a low level in the system, traditional antivirus software is often ineffective at detecting and removing them.
What is Secure Boot?
Secure boot is a feature in UEFI that ensures that only trusted software is loaded during the boot process. When a computer starts up, the UEFI firmware checks the digital signature of the boot loader and any other software that is loaded during the boot process. If the digital signature is valid and the software is trusted, it is loaded into memory and the boot process continues. If the digital signature is invalid or the software is not trusted, the boot process is halted and the user is notified.
Secure boot is designed to prevent unauthorized software from loading during the boot process. This can help protect against rootkits, bootkits, and other types of malware that infect the boot process.
What is BlackLotus?
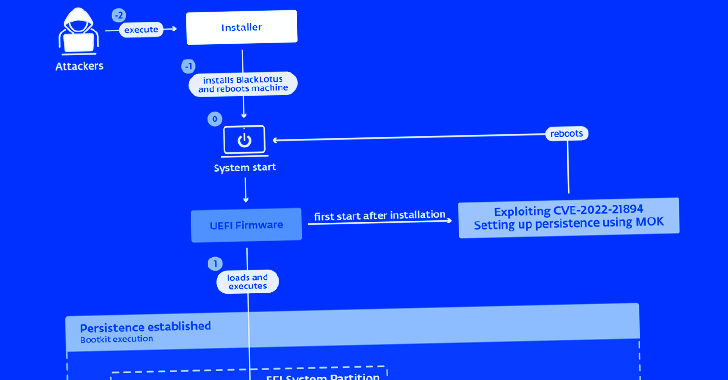
BlackLotus is a new UEFI bootkit malware that was discovered by security researchers in February 2023. BlackLotus is capable of bypassing secure boot on Windows 11, which is a significant accomplishment for malware developers.
BlackLotus works by infecting the UEFI firmware of a computer and then loading a malicious boot loader during the boot process. Because the boot loader has a valid digital signature, it is able to bypass secure boot and load the rest of the malware into memory.
Once BlackLotus is installed on a computer, it can be used to steal sensitive information, monitor user activity, and carry out other malicious activities. Because BlackLotus operates at such a low level in the system, it is difficult to detect and remove using traditional antivirus software.
How Does BlackLotus Bypass Secure Boot on Windows 11?
BlackLotus is able to bypass secure boot on Windows 11 by exploiting a vulnerability in the UEFI firmware. The vulnerability allows BlackLotus to modify the UEFI firmware in such a way that it is able to load a malicious boot loader during the boot process.
The vulnerability that BlackLotus exploits is not unique to Windows 11; it has been present in UEFI firmware for several years. However, Microsoft has made significant improvements to the secure boot process in Windows 11, which makes it more difficult for malware to bypass secure boot.
Despite these improvements, BlackLotus was still able to bypass secure boot on Windows 11. This underscores the importance of continued research and development in the area of computer security.
What Can You Do to Protect Yourself?
If you are running Windows 11, there are several steps you can take to protect yourself against UEFI bootkit malware like BlackLotus. Here are a few suggestions:
1. Keep your computer up-to-date with the latest security updates and patches. Microsoft is releasing updates to address security vulnerabilities, so it is important to make sure your system is up-to-date. 2. Use a reputable antivirus software. While traditional antivirus software may not be effective at detecting and removing UEFI bootkits, it can still be useful for detecting other types of malware.
3. Enable secure boot and other security features in your UEFI firmware. While BlackLotus was able to bypass secure boot, enabling this feature can still help protect against other types of malware.
4. Be cautious when downloading and installing software from untrusted sources. Malware often spreads through fake software downloads or software that has been tampered with.
5. Consider using a dedicated security solution that specializes in UEFI firmware and boot process protection. These solutions can provide an extra layer of protection against UEFI bootkits and other low-level threats.
In conclusion, BlackLotus's ability to bypass secure boot on Windows 11 highlights the importance of ongoing research and development in the area of computer security. As malware threats continue to evolve, it is important for users and security experts alike to stay vigilant and take proactive steps to protect against attacks.
1. Keep your computer up-to-date with the latest security updates and patches. Microsoft is releasing updates to address security vulnerabilities, so it is important to make sure your system is up-to-date. 2. Use a reputable antivirus software. While traditional antivirus software may not be effective at detecting and removing UEFI bootkits, it can still be useful for detecting other types of malware.
3. Enable secure boot and other security features in your UEFI firmware. While BlackLotus was able to bypass secure boot, enabling this feature can still help protect against other types of malware.
4. Be cautious when downloading and installing software from untrusted sources. Malware often spreads through fake software downloads or software that has been tampered with.
5. Consider using a dedicated security solution that specializes in UEFI firmware and boot process protection. These solutions can provide an extra layer of protection against UEFI bootkits and other low-level threats.
In conclusion, BlackLotus's ability to bypass secure boot on Windows 11 highlights the importance of ongoing research and development in the area of computer security. As malware threats continue to evolve, it is important for users and security experts alike to stay vigilant and take proactive steps to protect against attacks.
Comments
Post a Comment