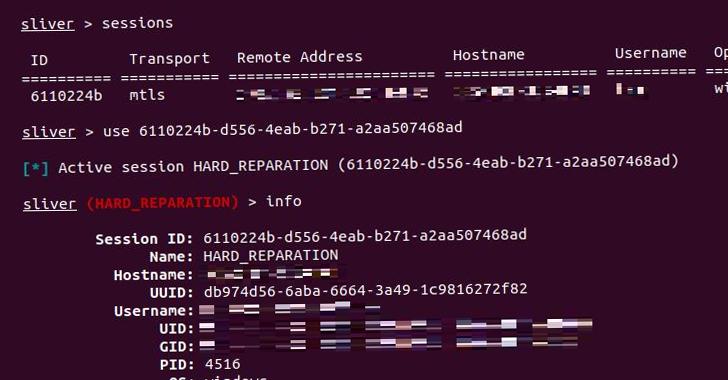
A new cybersecurity threat has emerged as hackers have been found to exploit vulnerabilities in the Sunlogin remote access software to deploy the Sliver Command and Control (C2) framework. The Sliver C2 framework is a malicious tool used by hackers to gain unauthorized access to victim's systems and steal sensitive information.
The exploitation of vulnerabilities in Sunlogin highlights the importance of keeping software and systems up-to-date and regularly patching any known security vulnerabilities. Organizations should also restrict network access to only necessary systems and users and implement strong password policies to help prevent unauthorized access to their systems.
In addition, organizations should regularly assess their cybersecurity posture and identify any gaps in their existing security measures. This may include conducting security audits, implementing multi-factor authentication, and regularly updating software and systems.
It is also important for organizations to educate their employees about the dangers of cyber attacks and how to recognize and avoid phishing attacks and other tactics used by hackers to spread malware.
In conclusion, the exploitation of vulnerabilities in Sunlogin to deploy the Sliver C2 framework serves as a reminder of the importance of having a comprehensive cybersecurity strategy in place to protect against cyber attacks. By taking proactive steps to protect against cyber threats and being prepared to respond in the event of an attack, organizations can minimize the risk of a successful cyber attack.
Comments
Post a Comment