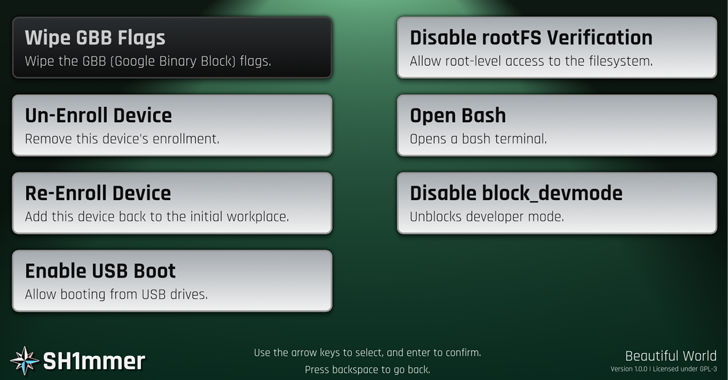
A new SH1MMER exploit has been discovered that can unenroll managed ChromeOS devices, making them vulnerable to malicious attacks. The exploit takes advantage of a flaw in the ChromeOS update process to unenroll the devices, allowing attackers to install malware, steal sensitive information, or gain unauthorized access to the affected systems.
SH1MMER is a type of malware that targets Chromebook devices, which are widely used in schools, businesses, and other organizations. The malware is designed to be highly persistent and difficult to remove, making it a significant threat to the security of managed ChromeOS devices.
The new SH1MMER exploit works by exploiting a vulnerability in the ChromeOS update process, allowing the attacker to unenroll the device from its management console. This gives the attacker complete control over the affected system, making it easy for them to install malware, steal sensitive information, or launch further attacks on the organization.
To prevent this type of attack, organizations must be vigilant in managing and securing their ChromeOS devices, and must take steps to educate their employees on how to identify and avoid malware infections. This includes regularly updating software and security controls, implementing firewalls and anti-virus software, and monitoring their systems for signs of unusual activity.
Consumers should also be cautious when using ChromeOS devices, and should be aware of the risks posed by malicious attacks. They should consider using alternative devices or operating systems where possible, or take steps to secure their ChromeOS devices, such as using strong passwords, enabling two-factor authentication, and regularly updating their software and security controls.
The discovery of the new SH1MMER exploit highlights the need for organizations and consumers alike to be proactive in protecting their devices from malicious attacks. The consequences of a successful malware infection can be devastating, so it is essential that organizations take action to reduce their risk.
Comments
Post a Comment