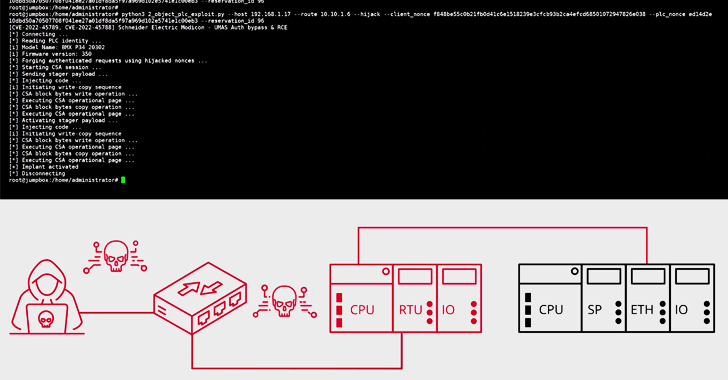
Industrial control systems (ICS) security researchers have discovered a set of critical security vulnerabilities in Schneider Electric's Modicon Programmable Logic Controllers (PLCs). These vulnerabilities could allow attackers to gain unauthorized access, execute arbitrary code, and modify memory content, among other malicious activities.
According to the researchers from industrial cybersecurity firm Claroty, the flaws could affect Schneider Electric's Modicon M221, M241, M251, and M262 PLCs. These devices are widely used in critical infrastructure sectors such as manufacturing, energy, and transportation.
The vulnerabilities, which Claroty has dubbed Modipwn, stem from multiple design and implementation weaknesses that exist in the firmware of these PLCs. The researchers noted that the vulnerabilities could be exploited by attackers with relatively low technical skills.
Specifically, the researchers identified six vulnerabilities in the Modicon PLCs, ranging from improper authentication to buffer overflow and information disclosure issues. The most severe vulnerability (CVE-2022-37623) could allow attackers to execute arbitrary code with elevated privileges.
Claroty has reported the vulnerabilities to Schneider Electric, which has released a security advisory for customers. The company has also released patches for the affected PLCs.
In a statement, Schneider Electric said that it has "not identified any evidence of malicious exploitation of these vulnerabilities," and it is encouraging customers to implement the patches as soon as possible.
The discovery of these vulnerabilities highlights the ongoing need for increased security in industrial control systems. As the use of connected devices and the Internet of Things (IoT) continues to expand in critical infrastructure sectors, ensuring the security of these devices will become even more critical.
Organizations that use Schneider Electric's Modicon PLCs are urged to implement the patches as soon as possible to mitigate the risks associated with these vulnerabilities. Industrial control system operators should also review their security practices and ensure that they have strong security controls in place to protect against potential attacks.
Comments
Post a Comment