New Wave of PlugX Trojan Attacks Disguised as Legitimate Windows Debugger Tool: How to Protect Your Computer and Data
Cybersecurity researchers have recently discovered that the notorious PlugX Trojan is being used in a new series of attacks. What's surprising about these attacks is that the Trojan is disguised as a legitimate Windows debugger tool, making it harder to detect and avoid. In this article, we'll take a closer look at the PlugX Trojan and its latest attacks, and provide some tips on how to protect your computer and data.
What is the PlugX Trojan?
The PlugX Trojan is a type of malware that is often used by cybercriminals to gain access to and control over infected computers. Once installed on a victim's computer, the Trojan can give attackers remote access to the machine, allowing them to steal sensitive data, install additional malware, and carry out other malicious activities.
One of the key features of the PlugX Trojan is its ability to evade detection. The malware can use various methods to hide its presence on the infected machine, making it difficult for antivirus software and other security measures to detect and remove it.
How is the PlugX Trojan being used in the latest attacks?
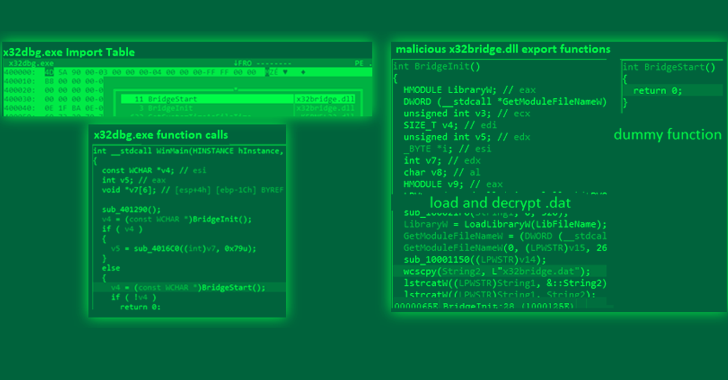
In the latest series of attacks, the PlugX Trojan is being disguised as a legitimate Windows debugger tool. The attackers are using a tool called "Microsoft Windows SDK Debugging Tools" to disguise the Trojan.
This tool is a legitimate debugging tool that is used by developers to debug and troubleshoot software applications. However, the attackers have modified the tool to include the PlugX Trojan, allowing them to use it as a backdoor to gain access to infected machines.
Once the Trojan is installed on a victim's machine, it can be used by attackers to steal sensitive data, install additional malware, and carry out other malicious activities. The Trojan can also give attackers remote access to the machine, allowing them to take control of the computer and use it for other nefarious purposes.
How can you protect your computer and data from the PlugX Trojan?
There are several steps you can take to protect your computer and data from the PlugX Trojan and other similar malware:
Keep your software up-to-date: One of the key ways that attackers can exploit vulnerabilities on your computer is by using outdated software. Make sure that you regularly update your software, including your operating system, web browser, and other applications.
Use antivirus and anti-malware software: Make sure that you have antivirus and anti-malware software installed on your computer. These tools can help detect and remove malware, including the PlugX Trojan.
Be cautious when opening email attachments: Malware can often be spread through email attachments, so be cautious when opening attachments from unknown senders. If you're not sure about an attachment, don't open it.
Avoid suspicious websites: Be cautious when browsing the web, and avoid visiting suspicious or untrustworthy websites. These sites can often contain malware that can infect your computer.
Use strong passwords: Make sure that you use strong passwords for your accounts, and don't reuse passwords across multiple accounts. This can help prevent attackers from gaining access to your accounts and data.
Conclusion
The PlugX Trojan is a dangerous type of malware that is often used by cybercriminals to gain access to and control over infected computers. In the latest series of attacks, the Trojan is being disguised as a legitimate Windows debugger tool, making it harder to detect and avoid. To protect your computer and data from the PlugX Trojan and other similar malware, make sure that you keep your software up-to-date, use antivirus and anti-malware software, be cautious when opening email attachments and visiting suspicious websites, and use strong passwords for your accounts.
Comments
Post a Comment