Hackers Exploit Microsoft's "Verified Publisher" OAuth to Breach Corporate Emails, Threatening Business Continuity
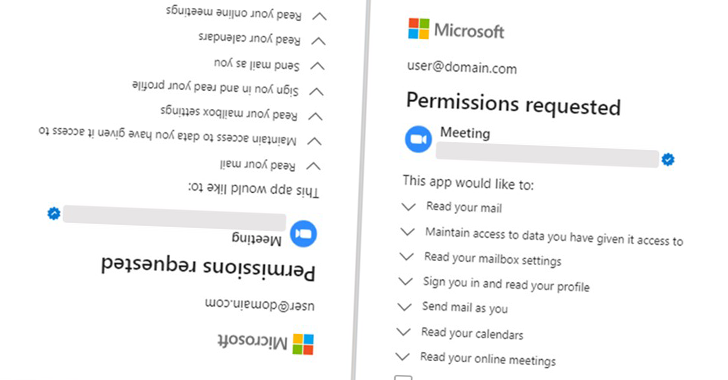
Hackers have been found to have abused Microsoft's "Verified Publisher" OAuth apps to breach corporate email accounts. This new attack vector allows hackers to bypass security controls and gain unauthorized access to sensitive corporate data.
The attack works by using Microsoft's OAuth authentication protocol, which is designed to allow third-party apps to access user data without requiring users to share their passwords. In this case, hackers have created fake OAuth apps that appear to be from verified publishers, tricking users into granting access to their email accounts.
Once the hackers have access to a user's email account, they can use it to gather sensitive information, steal data, and launch further attacks on the victim's organization. They can also use the compromised email account to spread malware to other users within the organization.
To prevent this type of attack, organizations must be vigilant in monitoring the OAuth apps that are connected to their email accounts, and must take steps to educate their employees on how to identify and avoid suspicious apps.
In addition, organizations should consider implementing multi-factor authentication for their email accounts, which can greatly reduce the risk of unauthorized access. They should also regularly update their security controls and software, and monitor their networks for signs of unusual activity.
The abuse of Microsoft's "Verified Publisher" OAuth apps highlights the need for organizations to be proactive in managing the risks posed by third-party software and services. The consequences of a successful email breach can be devastating, so it is essential that organizations take action to reduce their risk.
Comments
Post a Comment