ESXiArgs Ransomware Hits European Organizations, Targeting Virtual Machines on VMware's ESXi Hypervisor
A new ransomware strain, known as ESXiArgs, has recently been discovered to have infected over 500 systems across several European countries, including Spain, Italy, and Belgium. The ransomware is designed to target virtual machines (VMs) running on VMware's ESXi hypervisor and encrypts files with a .esxiargs extension.
ESXiArgs ransomware is distributed through phishing emails that contain malicious attachments, disguised as legitimate documents. Once the victim opens the attachment, the ransomware is deployed and begins to encrypt files on the target's system.
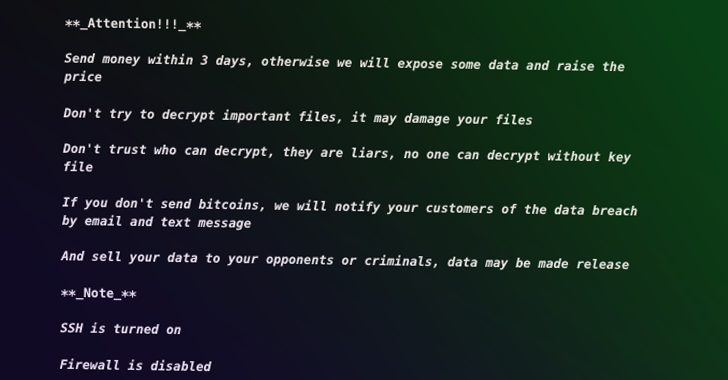
According to cybersecurity researchers, ESXiArgs is a sophisticated and well-designed ransomware that is difficult to decrypt. The ransomware operators demand a ransom payment in exchange for the decryption key, which typically ranges from a few thousand to tens of thousands of euros.
The ransomware is particularly concerning because it targets VMs on the ESXi hypervisor, which is commonly used by businesses to run multiple virtual machines on a single physical server. This means that an attack could potentially impact multiple systems within a single organization, causing widespread disruption and potentially significant financial losses.
While ESXiArgs is a relatively new ransomware strain, it is likely to continue to be a threat to organizations as it evolves and adapts to new security measures. To protect against such attacks, organizations should implement a multi-layered approach to cybersecurity, including regular backups, software patches and updates, and employee training on how to identify and avoid phishing emails.
In addition, companies should ensure they have a robust incident response plan in place in case of a ransomware attack, to minimize the impact and potential financial losses.
Comments
Post a Comment