PY#RATION: New Python-based RAT Emerges as a Threat to Cybersecurity, Utilizing WebSocket for Command and Control and Data Exfiltration
In recent years, the use of Remote Access Trojans (RATs) has become a popular tactic among cybercriminals. These tools allow attackers to gain remote control of a victim's computer and use it for a variety of malicious activities, such as stealing sensitive data, distributing malware, and conducting reconnaissance.
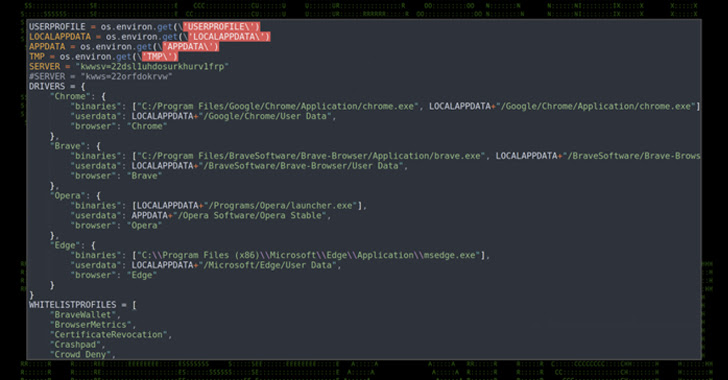
One of the newest RATs to be discovered is PY#RATION, a Python-based malware that is delivered via a malicious Microsoft Office document. Once it is installed on the victim's computer, PY#RATION uses the WebSocket protocol to communicate with its Command and Control (C2) server, which is used to control the malware and exfiltrate data from the infected machine.
Unlike traditional RATs that rely on traditional protocols, such as HTTP or TCP, PY#RATION uses WebSockets, a real-time, bidirectional communication protocol that is designed for web applications. This allows the malware to establish a persistent connection with the C2 server, which makes it difficult to detect and block.
PY#RATION also includes a number of features that allow it to evade detection and analysis. For example, it uses a custom packer to encrypt its payload, and it includes anti-debugging and anti-sandboxing techniques to evade analysis. Additionally, it uses a technique called "domain shadowing" to create subdomains on legitimate domains, which makes it difficult to block the C2 server.
The use of RATs like PY#RATION highlights the importance of using advanced threat detection and response tools to protect against these types of attacks. This includes using endpoint protection software that can detect and block malicious activity, as well as monitoring network traffic for signs of suspicious activity. Additionally, organizations should have incident response plans in place to quickly respond to and contain any suspected breaches.
In conclusion, PY#RATION a new Python-based RAT uses WebSocket for C2 and Data Exfiltration, it's a new and sophisticated form of attack and requires organizations to take a proactive approach to cyber security, in order to protect against these types of advanced threats.
Comments
Post a Comment